Cybercrime measures aim to weed out ‘rogue IoT’
TOKYO - The government is working to establish comprehensive security measures for IoT (internet of things) devices ahead of the 2020 Tokyo Olympics. It plans to probe the domestic network to identify IoT devices that are susceptible to cyber-attacks and alert the devices’ users to the potential danger.
However, legal barriers stand in the way of these measures actually being effective. The government, therefore, plans to continue reviewing the Law on Unauthorized Computer Access Prohibition and the Telecommunications Business Law.
Devices with flimsy security
“We want to manage to eradicate rogue IoT,” said an official of the Internal Affairs and Communications Ministry, who will be in charge of a large-scale investigation of IoT devices.
Rogue IoT refers to IoT devices that are not properly maintained and thus have only flimsy security, leaving them susceptible to being easily operated by an external party without the user’s knowledge.
Refrigerators and cameras that connect to the internet are indeed handy, but such IoT devices are at risk and are often still used with their original default IDs and passwords or lack updates to vulnerable software security. More easily than they can personal computers, cyber criminals can misuse these devices as “tools” in cyber-attacks.
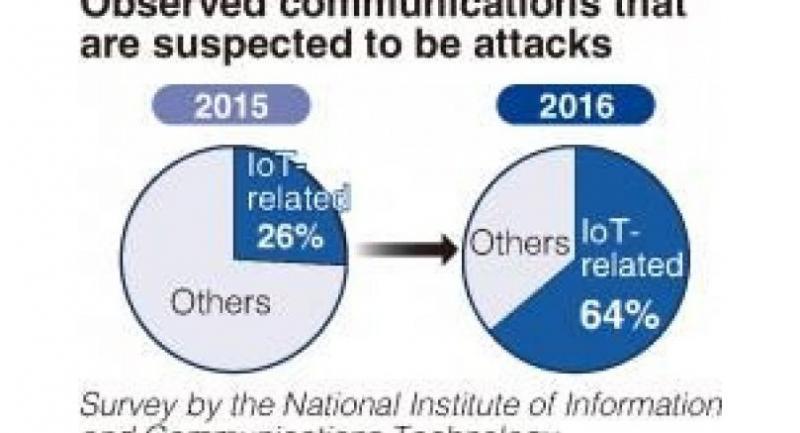
Last autumn, over 500,000 IoT devices were infected with a virus called “Mirai.” The devices were utilized as “stepping stones” in a larger-scale cyber-attack, which was also aided by rogue IoT.
First, cyber criminals used a method called “port scanning” (see below) to locate devices with characteristic IoT device ports left open. These ports are like a window through which telecommunications are received. If they are needlessly left open, they become an easy point of entry for criminals.
Once they find a device with an open window, criminals will then look for a “key” to open the safe. In other words, they will try to input ID and password combinations to see if they can open the lock. When Mirai hit, criminals methodically went through about 60 simple factory default user IDs and passwords until they got a hit. They used this method to successfully infiltrate over 500,000 devices. In other words, that many vulnerable devices had been left unprotected.
Exemptions required
To turn this method on its head, “We should be able to protect devices by using the exact same method of scanning for open ports and running though potential IDs and passwords to identify rogue IoT, and then encouraging the users of these devices to update their security, thereby preventing future attacks,” says the communications ministry official.
That is the aim of this government initiative. However, a person related to the matter said, “If the current situation is left unattended, we can’t even deal with 10 percent of the devices we need to.” The law is getting in the way.
First, the Law on Unauthorized Computer Access Prohibition prohibits anyone from conducting unauthorized access. Even if the purpose is investigation, inputting another person’s user IDs and passwords without their permission and infiltrating their computer is punishable by the law.
In addition, specific standards have not been identified as to whether it is legal to enter factory default passwords that are made public by manufacturers.
It is still unclear how far the investigation will attempt to go. But even if, for instance, they use the factory default IDs and passwords made public by the manufacturer, the effort will fall short of the 60 combinations tried by the perpetrators of the Mirai virus, enabling them to find only a portion of vulnerable devices.
Takayoshi Hojo, an attorney who is well versed in cybercrime, said: “At present, all we get are attacks from cyber criminals, and the people who are supposed to protect us can’t accurately grasp what is going on. The Law on Unauthorized Computer Access Prohibition needs to be revised so that some research institutions are exempt.”
Rethink related laws
Even if vulnerable devices are found, another barrier looms when it comes to informing users: the Telecommunications Business Law.
The law stipulates that telecommunications operators are prohibited from infringing on the “privacy of communications.” The law is so strict that it pertains not only to the content of these communications, but also stipulates that the identification of users from IP addresses is a violation.
The communications ministry has been holding meetings with experts on how to deal with cyber-attacks for several years now and has clarified its position on each issue raised. It has now permitted the identification and isolation of terminals that are used to spread viruses and participate in attacks.
However, it has yet to decide its position on cases where the device’s security is vulnerable but it is unknown whether it has been infected with viruses.
Thus, only cases that present a major threat will result in the notification of users at this time.
“It takes time for a panel of experts to investigate a problem every time one occurs, and their response comes too late,” said a person related to the matter. “Since we’re constantly faced with new cyber-attack methods, isn’t it time that we fundamentally changed the law?”
In Germany, the law on telecommunications has been revised so that telecommunications businesses that discover a terminal has been infected with viruses and used in cyber-attacks are obligated to report this to the user.
Keep pace with cyberspace
The responsibilities of IoT device manufacturers and sellers also require review. It is important in the future to make products safe from the development stage onward, and to properly deal with products already on the market.
But there is currently no legal basis to demand manufacturers and sellers take these steps.
Efforts are under way to force manufacturers to take responsibility for weaknesses in IoT devices. The U.S. Federal Trade Commission, for example, sued manufacturer “D-Link” in January for not adequately addressing the vulnerability of their routers.
The government plans to use the current investigation to determine the legal issues involved, and to begin to consider necessary changes to the law. But IoT is only one sphere in which legislation cannot keep pace with changes in cyberspace.
Take, for example, virus databases used overseas. Using such databases for research purposes is said to be legal, but the specific circumstances under which the usage would be regarded as for research are unclear. It is therefore difficult to take the plunge and construct a virus database in the country.
Hojo says, “The government needs to eliminate this gray area by drawing up guidelines that show what is possible and what is forbidden under current laws.”
Everyday devices at risk too
The current IoT investigation aims to identify devices that are vulnerable to cyber-attacks, from IoT devices used in major infrastructure to those found in the home such as network cameras and routers. The government plans to work with telecommunications operators to identify users and alert them of their device’s vulnerability, as well as compile a database to share with other parties concerned and use to counter cyber-attacks.
-- Port scanning
A signal is sent to all the ports on an information device to search for an active port. If an IP address can be likened to the “address” of a communications terminal, the ports are comparable to the terminal’s “windows.” Port scanning is like someone knocking on each window of that address to see whether it is open.
